How to Leak to The Intercept
WHISTLEBLOWING - SURVEILLANCE, 2 Feb 2015
People often tell reporters things their employers, or their government, want to keep suppressed. But leaking can serve the public interest, fueling revelatory and important journalism.
This publication was created in part as a platform for journalism arising from unauthorized disclosures by NSA contractor Edward Snowden. Our founders and editors are strongly committed to publishing stories based on leaked material when that material is newsworthy and serves the public interest. So ever since The Intercept launched, our staff has tried to put the best technology in place to protect our sources. Our website has been protected with HTTPS encryption from the beginning. All of our journalists publish their PGP keys on their staff profiles so that readers can send them encrypted email. And we’ve been running a SecureDrop server, an open source whistleblower submission system, to make it simpler and more secure for anonymous sources to get in touch with us.
But caution is still advised to those who want to communicate with us without exposing their real-world identities.
What Not to Do
If you are a whistleblower trying to figure out the best way to contact us, here are some things you should not do:
Don’t contact us from work. Most corporate and government networks log traffic. Even if you’re using Tor, being the only Tor user at work could make you stand out. If you want to leak us documents that exist in your work environment, first remove them from work and submit them using a personal computer on a different network instead.
Don’t email us, call us, or contact us on social media. Most of the ways that people communicate over the Internet or phone networks are incredibly insecure. Even if you take the time to learn how to encrypt your communications with us, your metadata will remain in the clear. From the standpoint of someone investigating a leak, who you communicate with and when is all it takes to make you a prime suspect, even if the investigators don’t know what you said.
Don’t tell anyone that you’re a source. Don’t risk your freedom by talking to anyone about leaking documents. Even if you plan on coming out as the leaker at some point in the future, you have a much better chance of controlling the narrative about you if you are deliberate.
As journalists we will grant anonymity to sources if the circumstances warrant it — for example, when a source risks recrimination by disclosing something newsworthy. If we make such an agreement with you, we will do everything in our power to prevent ourselves from being compelled to hand over your identity.
That said, in extreme cases, the best way to protect your anonymity may be not to disclose your identity even to us.
What to Worry About
And here are some things you should be aware of:
Be aware of your habits. If you have access to secret information that has been leaked, your activities on the internet are likely to come under scrutiny, including what sites (such as The Intercept) you have visited or shared to social media. Make sure you’re aware of this before leaking to us, and adjust your habits well before you decide to become our source if you need to. Tools like Tor (see below) can help protect the anonymity of your surfing.
Compartmentalize and sanitize. Keep your leaking activity separate from the rest of what you do as much as possible. If you need to use email, social media, or any other online accounts, don’t use your normal accounts that are connected to you. Instead, make new accounts for this purpose, and don’t login to them from networks you normally connect to. Make sure you don’t leave traces related to leaking laying around your personal or work computer (in your Documents folder, in your web browser history, etc.).
If possible, use a completely separate operating system (such as Tails, discussed below) for all of your leaking activity so that a forensics search of your normal operating system won’t reveal anything. If you can’t keep things completely separate, then make sure to clean up after yourself as best as you can. For example, if you realized you did a Google search related to leaking while logged into your Google account, delete your search history. Consider keeping all files related to leaking on an encrypted USB stick rather than on your computer, and only plug it in when you need to work with them.
Strip metadata from documents. Many documents, including PDFs, images, and office documents, include metadata that could be used to deanonymize you. Our policy is to remove metadata ourselves before publishing anything, but you might want to remove it yourself. Tails (discussed below) includes a program called Metadata Anonymization Toolkit that can strip metadata from a variety of types of documents. If you’re somewhat techie you can convert your documents to PDFs and then use pdf-redact-tools to completely remove any information hiding in them. You could also choose to go analog: print out a copy of the documents and then re-scan them before submitting them to us (but be careful to securely shred your printout and not leave traces in your printer’s/scanner’s memory).
How to Actually Leak
Now that we have that straight, here’s how to go about contacting us securely:
Go to a public WiFi network. Before following any further directions, grab your personal computer and go to a network that isn’t associated with you or your employer, such as at a coffee shop. Ideally you should go to one that you don’t already frequent. Leave your phone at home, and buy your coffee with cash.
Get the Tor Browser. You can download the Tor Browser here. When you browse the web using the Tor Browser, all of your web traffic gets bounced around the world, hiding your real IP address from websites that you visit. If your network is being monitored, the eavesdroppers will only know that you’re using Tor but not what you’re doing. Websites that you visit will only know that you’re using Tor, but not who you are (unless you tell them). It sounds complicated, but it’s actually quite easy to use. In order to start a conversation with us using our SecureDrop server, you must use Tor.
Consider using Tails instead. If you are worried about your safety because of the information you’re considering leaking, it might be prudent to take higher security precautions than just using Tor Browser. If someone has hacked into your computer, for example, they’ll be able to spy on everything you do even if you’re using Tor. Tails is a separate operating system that you can install on a USB stick and boot your computer to. Tails is engineered to make it hard for you to mess up:
- Tails leaves no traces that it was ever run on your computer
- It’s non-persistent, which means that if you got hacked last time you were using Tails, the malware should be gone the next time you boot up
- All Internet traffic automatically goes through Tor, so it’s much harder to accidentally de-anonymize yourself
- It has everything that you need to contact us through SecureDrop built-in, as well as other popular encryption tools
- It’s the operating system that Edward Snowden, Glenn Greenwald, Laura Poitras, and I used to keep the NSA journalism safe from spies
It sounds complicated, and it is. But if you’re risking a lot, it’s probably worth the effort. You can find instructions for downloading and installing Tails here.
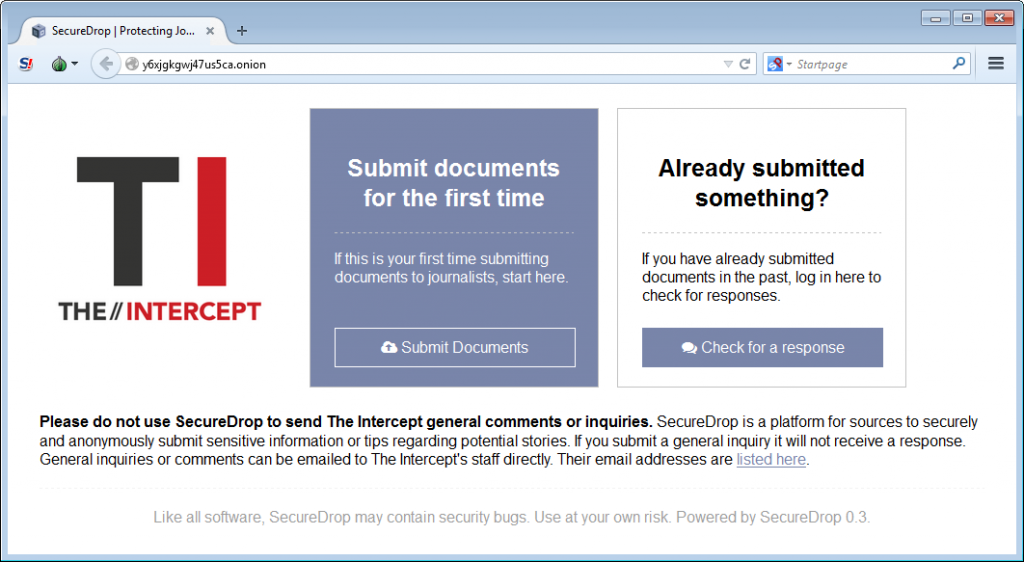
Use SecureDrop to communicate with us. You can use our SecureDrop server to securely and anonymously send us messages, read replies, and upload documents. If you have access to information that you’re considering leaking, you can use SecureDrop to just start a conversation with us until you’re comfortable sending in any documents. Or you could choose to dump a set of documents and never check back again.
You can access our SecureDrop server by going to http://y6xjgkgwj47us5ca.onion/ in Tor Browser. This is a special kind of URL that only works in Tor (even though the URL starts with “http://” and not “https://”, the connection between Tor Browser and our SecureDrop server is encrypted). This is what you’ll see:
To learn more about safely using SecureDrop as a source, check the official guide for sources document.
If you’d like to submit tips to us and your anonymity isn’t important, you can email tips@theintercept.com. If you’d like to use PGP encryption, you can find every journalist’s PGP public key on their staff profile.
Questions? Have further advice for would-be leakers? Post them in the comments below.
Go to Original – firstlook.org
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE: