Home-made Spy Drone Hacks WiFi Networks, Listens to Calls
TECHNOLOGY, 15 Dec 2014
Erin Van der Bellen, WUSA – TRANSCEND Media Service
It’s small. It’s bright yellow, and it’s capable of cracking Wi-Fi passwords, eavesdropping on your cell phone calls and reading your text messages. It’s an unmanned spy drone and it just landed in Washington, D.C.
Long-time friends and former Air Force buddies, Mike Tassey and Rich Perkins, describe their state-of-the-art cyber drone as hard to take down, hard to see and virtually hard to detect.
They built it in a garage, using off the shelf electronics to prove a drone can be used to launch cyber-attacks.
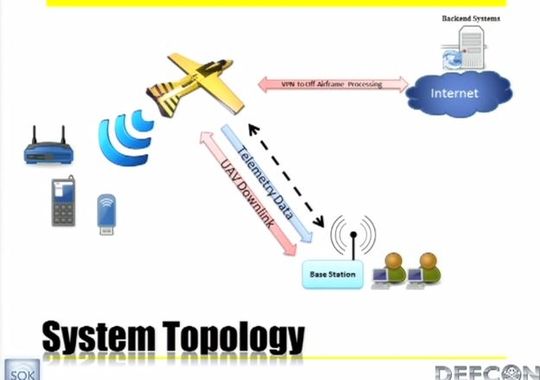
It needs a human for take-off and landing but once airborne, it can fly any pre-programmed route posing as a cell phone tower and tricking wireless cell phones.
While it’s flying those points, the spy drone has a number of antennas for picking up your cell phone conversation, for picking up blue tooth, and for picking up and monitoring Wi Fi signals.
Tassey and Perkins tested the drone in isolated conditions to avoid breaking laws or recording conversations other than their own.
“We passed telephone calls, hacked into networks, cracked the encryption on Wi-Fi access points all of that sort of evilness is possible,” said Tassey.
And now their spy drone has landed in Washington so everyone can see it.
“I think it’s fantastic to have an artifact like this in the Spy Museum,” said Vincent Houghton, International Spy Museum Curator.
“It’s the first of its kind, it’s a piece of modern espionage equipment,” said Houghton. “This is something governments should be doing and perhaps only government should be doing.
“If two guys from the Midwest can build this for six-thousand dollars in a garage, what can Iran do? What can nation states do?” said Rich Perkins.
The drone has a 50 mile range and while its creators chose a cyber-attack test, they say this technology can be used things like anti-IED missions and search and rescue operations.
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.