Leaked NSA Malware Threatens Windows Users Around the World
WHISTLEBLOWING - SURVEILLANCE, 17 Apr 2017

People sit in front of devices running the Microsoft Windows 8 operating system at a press conference launch of the system in New York City, on Oct. 25, 2012. Photo: Mario Tama/Getty Images
14 Apr 2017 – The ShadowBrokers, an entity previously confirmed by The Intercept to have leaked authentic malware used by the NSA to attack computers around the world, today released another cache of what appears to be extremely potent (and previously unknown) software capable of breaking into systems running Windows. The software could give nearly anyone with sufficient technical knowledge the ability to wreak havoc on millions of Microsoft users.
The leak includes a litany of typically codenamed software “implants” with names like ODDJOB, ZIPPYBEER, and ESTEEMAUDIT, capable of breaking into — and in some cases seizing control of — computers running version of the Windows operating system earlier than the most recent Windows 10. The vulnerable Windows versions ran more than 65 percent of desktop computers surfing the web last month, according to estimates from the tracking firm Net Market Share.
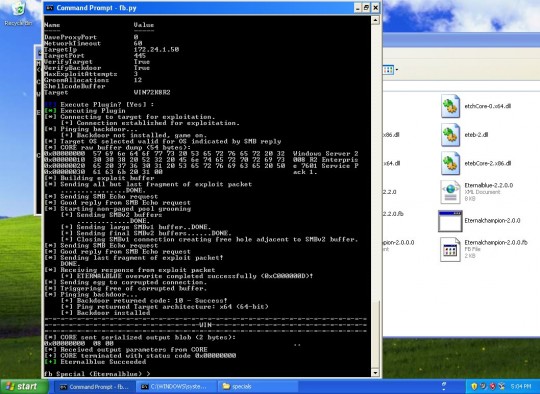
The crown jewel of the implant collection appears to be a program named FUZZBUNCH, which essentially automates the deployment of NSA malware, and would allow a member of agency’s Tailored Access Operations group to more easily infect a target from their desk.
According to security researcher and hacker Matthew Hickey, co-founder of Hacker House, the significance of what’s now publicly available, including “zero day” attacks on previously undisclosed vulnerabilities, cannot be overstated: “I don’t think I have ever seen so much exploits and 0day [exploits] released at one time in my entire life,” he told The Intercept via Twitter DM, “and I have been involved in computer hacking and security for 20 years.” Affected computers will remain vulnerable until Microsoft releases patches for the zero-day vulnerabilities and, more crucially, until their owners then apply those patches.
“This is as big as it gets,” Hickey said. “Nation-state attack tools are now in the hands of anyone who cares to download them…it’s literally a cyberweapon for hacking into computers…people will be using these attacks for years to come.”
Hickey provided The Intercept with a video of FUZZBUNCH being used to compromise a virtual computer running Windows Server 2008–an industry survey from 2016 cited this operating system as the most widely used of its kind.
httpv://vimeo.com/213263277
Susan Hennessey, an editor at Lawfare and former NSA attorney, wrote on Twitter that the leak will cause “immense harm to both U.S. intel interests and public security simultaneously.”
A Microsoft spokesperson told The Intercept “We are reviewing the report and will take the necessary actions to protect our customers.” We asked Microsoft if the NSA at any point offered to provide information that would help protect Windows users from these attacks, given that the leak has been threatened since August 2016, to which they replied “our focus at this time is reviewing the current report.” The company later clarified that “At this time, other than reporters, no individual or organization has contacted us in relation to the materials released by Shadow Brokers.”
Update: April 15, 2017
Late Friday night, Microsoft published a blog post stating that after an analysis of the ShadowBrokers leak, it had determined that most of the vulnerabilities were patched in a series of Windows updates released in March — updates that security researchers who analyzed the NSA tools apparently neglected to install. This means the exploits in question were not in fact “zero days” and that anyone running the most recent updates on software still supported by Microsoft is safe from the ShadowBrokers arsenal. But the timing of the patch in question is interesting: If Microsoft truly did not receive any help from the NSA, as it claims, the fact that it fixed a litany of holes vulnerable to secret NSA tools exactly a month before those tools were made public is an amazingly fortunate coincidence (curiously, Microsoft skipped the usual acknowledgements section with the patch, which typically nods to how they were informed of the threats fixed in a given update). At any rate, this is certainly good news for Windows users who keep their computers up to date, good news for Microsoft, and still very bad news for the NSA.
Update: April 14, 2017
This post has been updated with an additional comment from Microsoft.
________________________________________
 Sam Biddle – ✉sam.biddle@theintercept.com
Sam Biddle – ✉sam.biddle@theintercept.com
Go to Original – theintercept.com
DISCLAIMER: The statements, views and opinions expressed in pieces republished here are solely those of the authors and do not necessarily represent those of TMS. In accordance with title 17 U.S.C. section 107, this material is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. TMS has no affiliation whatsoever with the originator of this article nor is TMS endorsed or sponsored by the originator. “GO TO ORIGINAL” links are provided as a convenience to our readers and allow for verification of authenticity. However, as originating pages are often updated by their originating host sites, the versions posted may not match the versions our readers view when clicking the “GO TO ORIGINAL” links. This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more information go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
Read more
Click here to go to the current weekly digest or pick another article:
WHISTLEBLOWING - SURVEILLANCE: